Security Solution with TPM 2.0 Ubiquitous TPM Security Security software solution utilizing TPM with high tamper resistance

Ubiquitous TPM Security is a software solution for using "TPM (Trusted Platform Module)" defined by "TCG (Trusted Computing Group)" that establishes international industry standards.
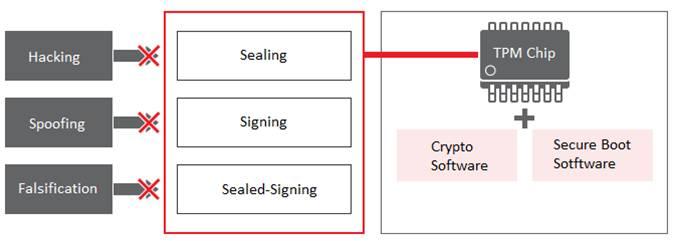
The TPM stablishes cryptographic boundary. Since it can not extract the secret key (encryption key) stored inside TPM, the security of the secret key (encryption key) is guaranteed. It also has functions necessary for security such as "creation of a pair of private key and public key", "public key cryptography", "calculation of hash value", "generation and verification of digital signature" .
These functions prevent "hacking", "spoofing", "falsification", and realize high security.
Features
- Solutions compatible with TPM 2.0 of latest specifications formulated by TCG can be deployed.
- Provide options to further enhance security level; "Ubiquitous TPM Secure Boot" to detect tampering with system configuration files
- Option to accelerate development of software using TMP chip; "Ubiquitous TCG Software Stack 2.0"
Member of Trusted Computing Group
Ubiquitous AI Corporation is an Adopter Member of Trusted Computing Group.


