Anti-tamper security solution for embedded devices Ubiquitous Securus Use secure hardware to prevent data leakage and tampering

In order to realize the high security which is indispensable for future IoT or M2M (Machine to Machine), the IoT device also needs to be secure. Ubiquitous Securus is a solution that strictly manages confidential data in order to realize the development and manufacture of secure IoT devices. By securely protecting confidential data using hardware's secure IP, we strongly support customers' secure IoT system development, preventing spoofing of devices, data leakage and tampering.
Ubiquitous AI Corporation helps to develop not only security measures for copyright protection technologies such as DTCP-IP and HDCP used for digital home appliances and IVI (In-Vehicle Infotainment) but development of Secure IoT devices that are rapidly spreading.
Features
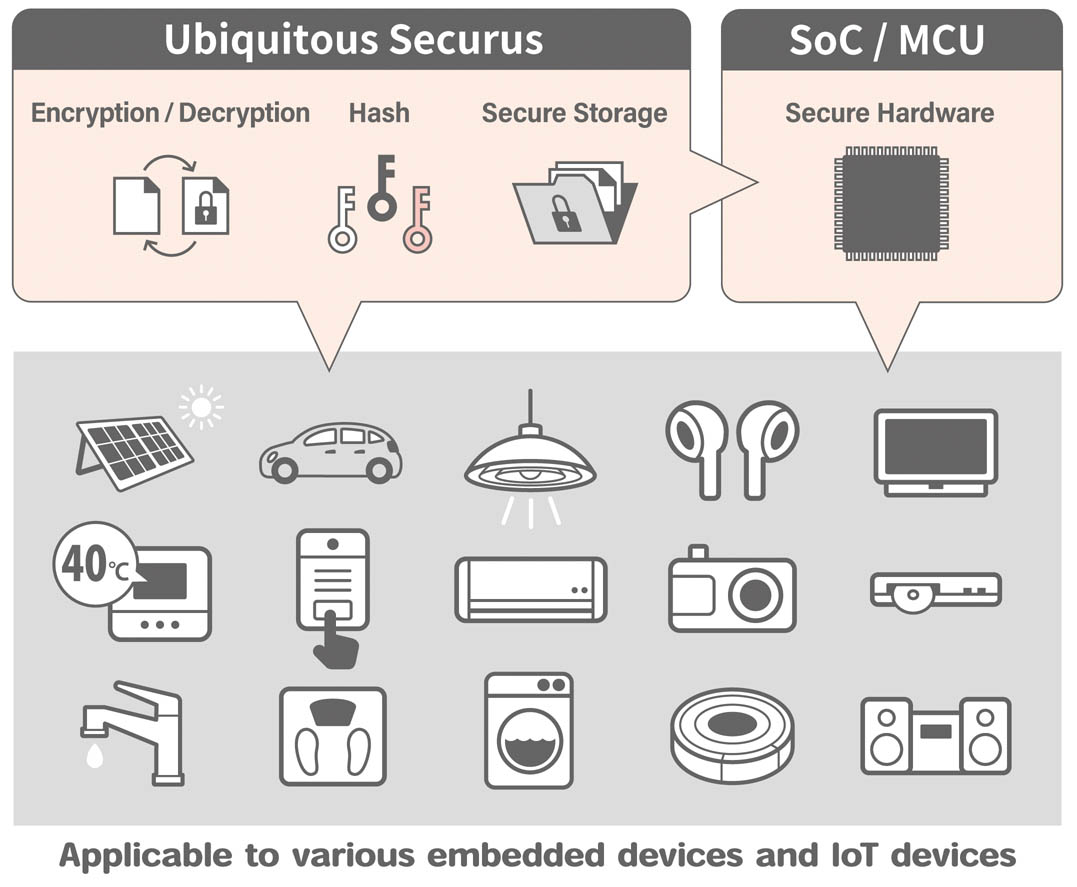
In addition to software processing, Ubiquitous Securus realizes high security by controlling and using secure hardware of SoC and MCU.
Comprehensive support from consulting before introduction to maintenance after manufacture enables to significantly reduce the development period and the burden on developers and to commercialize secure network equipment in a short period of time.
Strong confidential data management difficult to realize with software alone
By providing software that uses secure hardware, you can realize strong secret data management that is difficult to achieve with software alone.
Available for various semiconductors
Considering that different kinds of secure hardware are implemented due to generation change of SoCs, the porting layer is implemented with a design less affecting the upper application.
Provide comprehensive technical cooperation and support
In order to develop secure network equipment, comprehensive technical cooperation from planning, development, manufacturing to maintenance will shorten development period and burden on developers dramatically.

